DSM Offline Trade Safety — Final Technical Summary
Two people, face-to-face, phones in airplane mode: buyer Alice tries to double-spend; merchant Carol still keeps her merchandise safe.
1 Pre-Trade Cryptographic Context
| Primitive | Purpose | Size (offline) |
|---|---|---|
| Bilateral hash-chain H_{A\leftrightarrow X} | Per-relationship state log | 32 B/link |
| Device-wide SMT root R_n | One 32-byte commitment to all heads | 32 B |
| Spend-specific inclusion proof | Proves token T is present, unspent, uniquely keyed in R_n | \mathcal{O}(\log k)\!\approx\!200{-}400 B |
| Tripwire Theorem | Any fork ⇒ hash-collision impossible ⇒ attacker’s wallet bricks | Logic only |
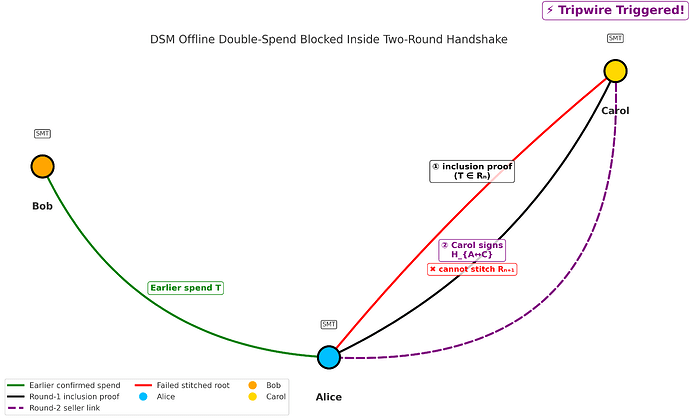
2 Two-Round Offline Payment Handshake
(Bluetooth or QR; completes in seconds.)
| Round | Data Exchanged | What Carol Verifies Offline |
|---|---|---|
| 1 – Challenge & Proof | Alice ➜ Carol • current root R_n • inclusion proof for token T |
Token T is unspent inside R_n. |
| 2 – Consume & Stitch | Carol ➜ Alice: new link H_{A\leftrightarrow C} that spends T Alice ➜ Carol: successor root R_{n+1} committing all heads incl. H_{A\leftrightarrow C} |
Carol checks: • H_{A\leftrightarrow C}\in R_{n+1} • R_n \!\rightarrow\! R_{n+1} is a valid forward-hash step. |
Pass: Carol receives a single stitched root R_{n+1} → wallet flashes FINAL.
Fail (fork): Alice cannot produce R_{n+1} → Tripwire fires; payment aborts.
3 Why Double-Spend Dies During the Handshake
- Earlier, Alice paid Bob, spending T and creating root R_{n+1}^{\,B}.
- Carol’s sale would require root R_{n+1}^{\,C} that also spends T.
- A single successor root cannot contain both spends ⇒ collision resistance forbids it.
- Alice fails to deliver R_{n+1} ➜ Carol’s wallet times out, shows Payment failed.
- Tripwire bricks Alice’s wallet for every future peer.
Outcome: Each honest merchant either receives irreversible value or receives nothing—no one hands over goods and loses out.
4 Operational Guarantees
| Property | Value |
|---|---|
| Finality latency | < 2 s offline |
| Data per trade | ≤ 500 B (root + proof + root) |
| Privacy | Merchant learns only their bilateral chain + two roots |
| Scalability | Works at 120 k TPS even on battery phones |
| Attack surface | Fork bricks attacker; cloning blocked by DBRW |
5 Bottom Line
DSM’s spend-specific inclusion proof plus the “return-the-stitched-root” round gives cryptographic finality in the same face-to-face encounter.
A merchant hands over the item only after holding an un-double-spendable asset.
No rip-offs, no chargebacks, zero exposure.
DSM is nearing production ready with a private beta soon - repo is currently private - but will be made public at public beta - [email protected] to get in touch