Hi all,
We just hacked a proof of concept tool for finding addresses that are being referenced by a smart contract: https://showme-1389.appspot.com/
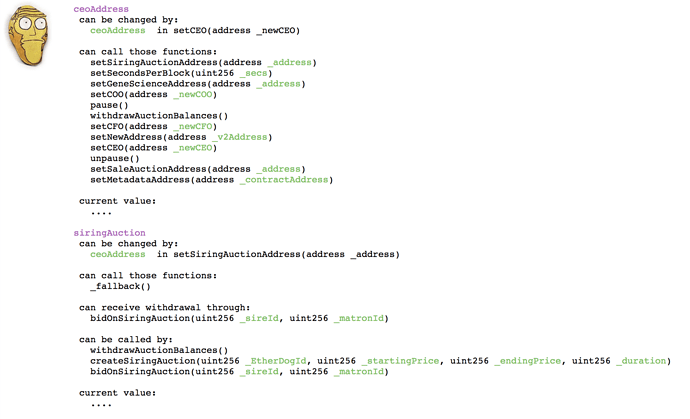
It uses API from the eveem.org symbolic decompiler to figure out stuff like this:
If anyone’s interested in how it’s done, you can check the github for sources, and also the intermediate language form that is the basis for the analysis, available here:
http://eveem.org/code/0x06012c8cf97bead5deae237070f9587f8e7a266d.json