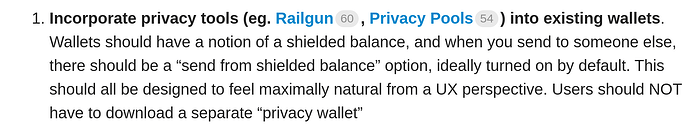
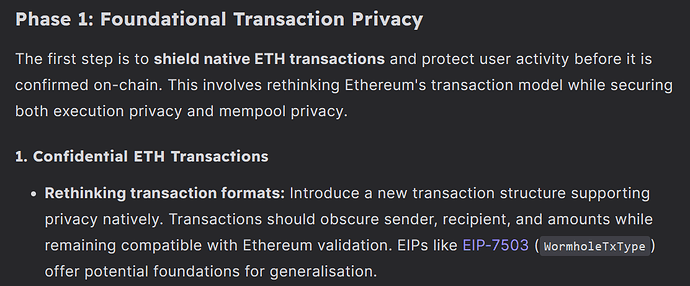
I contribute some user-centric inputs for consideration, to ensure that users aren’t too far behind as we progress on the roadmap.
1. Reference mental models
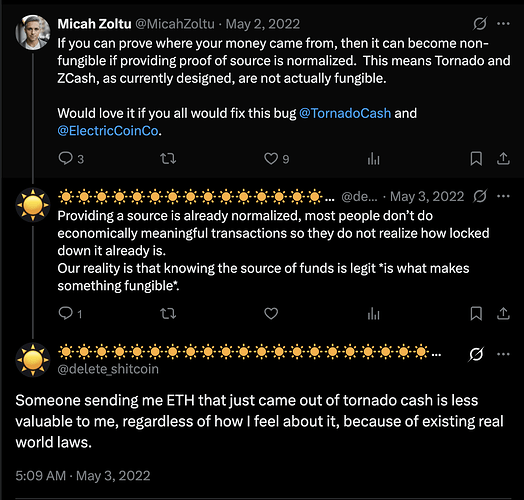
Understanding the who/what/when/where/how of privacy in crypto is Very Complicated.
Is it your real-world identity that is private, your string of transactions, or your IP address? Private from whom – your wallet, the RPC, random snoops? Is it private only now, or even after quantum computing? How do I choose between inclusion lists (Privacy Pools) or exclusion lists (Railgun)?
We need reference mental models that help users avoid drowning in complexity. (Recall Tim Berners-Lee’s original vision in the 1990s, that of course everyone would run a personal web server – nope, too hard.)
It’s not just for users’ sanity – clear and widely adopted mental models also help builders avoid using conventional but crypto-fatal mental models like adding telemetry to wallets… that include wallet seed phrases (Slope wallet).
Cryptozombies, Privacy Edition?
2. False sense of privacy
In cybersecurity there is a phenomenon called “false sense of security.” ChatGPT describes it:
“A false sense of security often arises when people adopt several cybersecurity tools—firewalls, antivirus software, VPNs—and assume they’re fully protected. The more tools they use, the safer they feel, even if those tools are misconfigured, outdated, or overlapping ineffectively. This illusion of safety is dangerous because it discourages deeper vigilance. True security requires more than stacking tools; it demands proper setup, regular testing, and a critical mindset.”
The same will happen when we are trying out privacy at so many different levels. Like the legions of early bitcoin users who mistook pseudonymity for anonymity, many are going to assume they have privacy when they don’t – at least not in the ways that they assumed.
How do we combat this? I imagine this is a task for someone at the 99th percentile of intelligence and memory – i.e. we need an AI-driven solution.
Perhaps it’s an AI agent that asks us what our priorities, fears, and constraints are, and then makes a recommendation on which identity to use with which application, based on the application’s privacy boundaries. Before we sign a transaction, we quiz it for a recommendation on where and how to transact. It monitors new privacy tools as they come live, evaluates them against our personalized criteria, and proposes updates to our design.
It helps us possess a justified sense of privacy.
3. Privacy is normal, but is it worth it?
Most people want privacy, but are not willing to pay the UX cost. Will the UX overhead in this roadmap be worth it for users?
Recall the transition from physical buttons to touchscreen glass in the evolution of smartphones:
In the mid-2000s, users were hesitant to switch from physical buttons to full glass touchscreens, associating them with laggy, stylus-dependent experiences. This changed with the 2007 iPhone, which introduced a smooth, finger-friendly capacitive touchscreen, multi-touch gestures, and a sleek design. As app ecosystems grew and large screens enhanced media consumption and navigation, touchscreens became essential. Social trends and minimalist design made button phones feel outdated. Gradually, users embraced the versatility of touchscreens.
I’ll never forget the pain of losing the ability to type surreptitiously under the table with my Blackberry’s physical keyboard, but the switch eventually became worth it because of the bajillions of apps on the App Store, and because everyone cool was getting an iPhone.
What will make it worth it for people who don’t bother with privacy today, to bother tomorrow? Before we start another round of infra fatigue, what’s our killer app?
4. Privacy Parties
Let’s throw privacy day parties: people spend a whole day transferring their assets over to private addresses, contracts, wallets, etc. Like with trusted set up ceremonies, we can harness community and memes to accelerate adoption – while boosting anonymity sets =D
Finally, on that note of pushing adoption – let’s highlight that privacy IS security. Privacy alone is too niche, too fraught with simplistic “what about the [insert vulnerable group]” arguments. Security is universally aspirational.