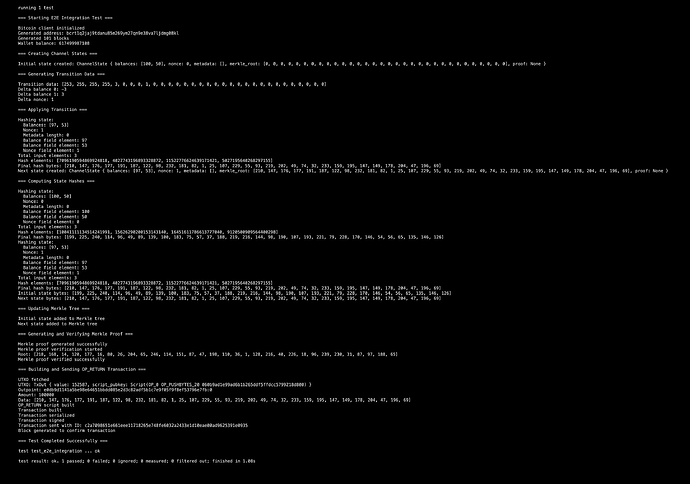
- Test Initialization:
• A Bitcoin client was initialized.
• Generated a new Bitcoin address and confirmed 101 blocks.
• Displayed the wallet balance. - Channel State Management:
• Created an initial channel state with balances and a Sparse Merkle Tree (SMT) root.
• Transition data was applied, including balance changes and nonce updates. - State Hashing:
• The initial and updated states were hashed using cryptographic primitives, with detailed hash computations logged. - Merkle Tree Operations:
• The Merkle tree was updated with the new state.
• A Merkle proof was generated and successfully verified. - OP_RETURN Transaction:
• An OP_RETURN transaction was built, signed, and sent.
• The transaction ID and details of the confirmed block were displayed. - Test Completion:
• The test concluded successfully with all assertions passing.
Description:
This screenshot captures a critical milestone for the Overpass Channels protocol—an end-to-end integration test showcasing its ability to securely manage state transitions and anchor data directly to Bitcoin.
• The protocol creates a trustless Layer 2 environment for Bitcoin, leveraging cryptographic proofs and Sparse Merkle Trees (SMTs) for scalable and verifiable state management.
• This test demonstrates:
• Successful state transitions between channel participants.
• Cryptographic state hashing and proof verification.
• Secure anchoring of channel state to Bitcoin via OP_RETURN transactions.
• Outcome: The test passed flawlessly, validating the trustless anchoring process and scalability potential of Overpass Channels.
This marks a significant step toward enabling scalable, private, and immutable Bitcoin-based applications.
NEW RELEASE DOCS:
#1 Developers and Researchers Documentation: Overpass
Framework with Perfect Mathematical Composability (PMC)
#2 Off-Chain Native Bitcoin: A Mathematical Framework for
True Layer 2 Value Overpass Protocol
The diagram above shows how with Overpass I have effectively managed to solve the Trilemma achieving “Perfect Mathematical Composability” which was thought to maybe only be theoretically possible and most deemed impossible. I wasn’t looking for it specifically. Just how to scale in general…I managed to identify it while Overpass was exhibiting certain key properties, but not all of them ideally and then I made some what felt like intuitive tweaks to the protocol and then realize that it was unique did some reading and found out there was already a name for it… PMC
This unlocks a whole new paradigm for Web3
TL;DR
Overpass’s architecture excels through random walk-based state transitions combined with Pederson hierarchy integration, enabling O(1) verification and explicit quantum resistance against both Grover’s and Shor’s algorithms while maintaining efficient state transitions across hierarchical layers.
Background
Traditional state update systems require complete Sparse Merkle Tree (SMT) path verification, resulting in O(log n) complexity. These introduce scalability challenges when applied to hierarchical systems like Overpass.
Random walk verification allows constant-time operations while directly complicating quantum attack vectors through structural integration with Pederson authentication paths.
Proposal
Overpass implements:
-
Random Walk State Transitions with Pedersen Integration:
- Constant-time verification through SMT random walks:
- Verifier validates state transition through random walk computation
- Pederson paths provide additional quantum resistance layer
- The transition is verified using ZKPs:\pi = \text{ZKP}(RW(s, k) \otimes P(h))
Where P(h) represents the Pedersen authentication path
- Constant-time verification through SMT random walks:
-
Quantum Attack Resistance:
- Random walks performed on SMT structure with Pedersen integration:H_{\text{new}} = H_{\text{old}} \oplus RW(s, k) \otimes P(h)
- Explicitly complicates Grover’s algorithm by requiring:O(2^{n/2}) \times O(2^{P(h)}) = O(2^{n/2 + P(h)})
- Defeats Shor’s algorithm by avoiding cyclic group structure:\nexists \text{ } g^x \text{ mod } p \text{ structure in } RW(s,k) \otimes P(h)
- Random walks performed on SMT structure with Pedersen integration:
Advantages
- Quantum Attack Resistance:
- Grover’s Algorithm: Required iterations increase exponentially
- Shor’s Algorithm: No underlying cyclic group to attack
- Efficient Proof Generation:
- Constant-time proof size and generation:
- Start Position → Random Walk+Pedersen → End Position
- Constant-time proof size and generation:
- ** Pedersen Integration Benefits**:
- Additional quantum resistance layer
- Maintains O(1) verification complexity
- Perfect Mathematical Composability:
- State updates integrate seamlessly with constant-time verification
Comparisons
- Traditional Quantum-Resistant Systems:
- Rely solely on increased computational complexity:O(2^{n/2}) \text{ for Grover's}
- Vulnerable to algorithmic improvements
- Rely solely on increased computational complexity:
- Cyclic Group Systems:
- Vulnerable to Shor’s algorithm:O(\log^3 n) \text{ quantum complexity}
- Fundamentally insecure against quantum attacks
- Vulnerable to Shor’s algorithm:
- Overpass:
- Combines structural and computational resistance:\text{Verify}(RW(s,k) \otimes P(h)) = O(1)\text{QuantumAttack} = O(2^{n/2 + P(h)})
- Combines structural and computational resistance:
Applications
- Post-Quantum State Systems:
- Explicitly resistant to known quantum attacks
- Hierarchical Authentication:
- Pedersen integration across all layers
- Future-Proof Protocols:
- Structural resistance to quantum algorithms
Conclusion
Overpass’s random walk-based verification with Pedersen integration achieves O(1) complexity while providing explicit resistance to both Grover’s and Shor’s algorithms. The combination of structural and computational quantum resistance, without sacrificing performance, represents a significant advancement in quantum-resistant state transition system design.