Following is the polynomial commitment scheme between Prover and Verfier. I was looking at the KATE scheme and I noticed it could be done differently and easier. Note that it doesn’t require trusted setup, nor attaching additional proof to the result F(t) for a challange t.
Let me know what you think. Is it useful? Can you break it?
Pairing
The pairing is a map e: G_1 \times G_2 \rightarrow G_T where G_1 and G_2 are additive groups and G_T is multiplicative group.
Both groups have generators. P for G_1 and Q for G_2. These are publically known.
Pairing e satisfies:
Commitment
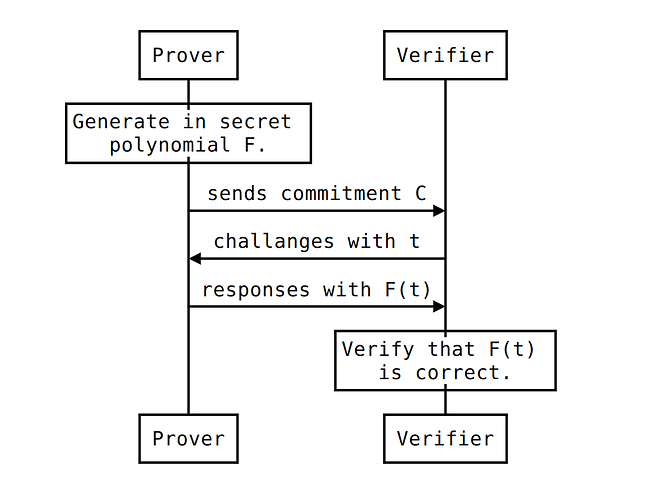
Prover has a secret polynomial F.
Firstly Prover generates two random secret numbers a and b. They are used to hide coefficients of F and compose new polynomial K.
Second step is projecting K on G2. It means multiplying all coefficients by Q. This creates new polynomial Z over G_2.
Final part of the commitment is hiding a on G_1 and b on G_2.
The commitment C to polynomial F can be send to Verifier.
Challange
Knowing C, Verifier can ask Prover to calculate F(t) for a given t.
Prover computes F(t) and sends the result back to the verifier.
Verification
Verifier knows: t, F(t) and C = (Z, M, N). To make sure F(t) is correct, the following check needs to be satisfied.
Reasoning
Following transforms right-hand side of the verification check to the left-hand side.

 to do it.
to do it.