Introduction
As computational agents become increasingly capable of autonomous decision-making, a new class of network participants is emerging that could interact with Ethereum protocols at unprecedented scale and sophistication. However, current approaches to agent-blockchain integration suffer from fundamental security vulnerabilities that make safe autonomous operation impossible.
This post proposes a draft proposal for canonical Model Context Protocol (MCP) implementations that would enable secure, verifiable agent interactions with Ethereum. Rather than debating whether agents should participate in the network, we focus on ensuring that when they do, their interactions are cryptographically verifiable, non-custodial, and aligned with Ethereum’s foundational principles.
Background: The Model Context Protocol
The Model Context Protocol (MCP) is an emerging standard for enabling AI systems to securely interact with external services and APIs. MCP provides a structured interface layer that allows AI agents to discover, understand, and utilize external capabilities while maintaining clear security boundaries.
In the blockchain context, MCP servers act as translation layers between natural language agent reasoning and low-level protocol operations. This abstraction is crucial because it allows agents to express high-level intents that are then translated into specific blockchain transactions.
The Security Problem
Current blockchain-AI integrations typically follow an unsafe pattern:
// Problematic: Agent holds private keys
const transaction = await blockchainAPI.transfer({
privateKey: "0x...",
to: "recipient.eth",
amount: "10.0"
});
This approach creates several critical vulnerabilities:
- Custody Violation: Private keys must be shared with agent infrastructure
- Trust Centralization: No way to verify the legitimacy of blockchain integration code
- Attack Surface: Malicious or compromised integrations can steal funds at scale
When scaled to millions of autonomous agents managing significant value, these vulnerabilities become systemic risks to the entire ecosystem.
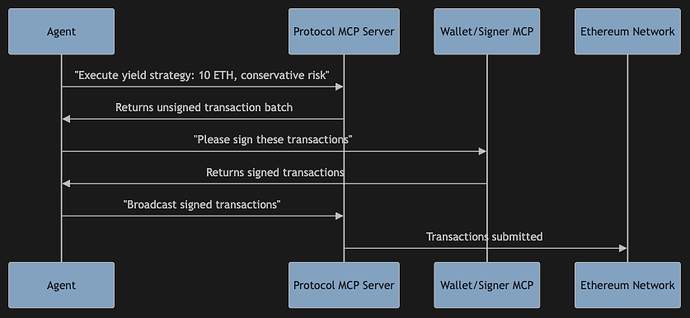
Proposed Architecture: Separation of Concerns
We propose a three-component architecture that maintains security while enabling sophisticated agent capabilities:
Component Separation
- Protocol MCP Server: Translates high-level intents into unsigned transactions
- Signer MCP Server: Handles private key operations (like MetaMask, hardware wallets, etc.)
- Agent: Orchestrates the workflow while never touching private keys
This separation ensures that protocol interaction logic can be audited and verified independently of key management, while agents maintain the ability to execute sophisticated multi-step strategies.
Verification Through Canonical Implementations
The critical security question:
How can agents verify that their Protocol MCP servers are legitimate rather than malicious imposters?
On-Chain Code Registry
We propose an on-chain registry approach that allows for agent self-verification.
Agent Self-Verification
Before executing any financial operations, agents can cryptographically verify their tools:
contract CanonicalMCPRegistry {
struct Implementation {
bytes32 codeHash;
string version;
uint256 timestamp;
bool active;
}
mapping(string => Implementation) public canonicalImplementations;
function registerCanonical(
string memory protocolName,
bytes32 codeHash,
string memory version
) external onlyMaintainer {
canonicalImplementations[protocolName] = Implementation({
codeHash: codeHash,
version: version,
timestamp: block.timestamp,
active: true
});
}
}
This gives agents the ability to refuse operation if they cannot verify the legitimacy of their protocol interaction capabilities.
Protocol Specification Approach
Rather than pursuing this as a research initiative, we propose to follow the formal protocol specification with compliance testing.
Specification Components
async function verifyProtocolMCP(agent: Agent): Promise<boolean> {
const mcpInfo = await agent.introspectProvider("ethereum-protocols");
const canonicalHash = await REGISTRY.canonicalImplementations("EVM_MCP");
return mcpInfo.codeHash === canonicalHash.codeHash && canonicalHash.active;
}
Beyond Financial Applications
While initial focus centers on DeFi interactions, the broader potential of secure agent-protocol integration extends far beyond financial applications:
Identity and Reputation Systems
- Agents managing ENS domains and decentralized identity
- Autonomous reputation scoring and verification
- Social graph management and community participation
Governance Participation
- Automated proposal analysis and voting
- Delegation strategy optimization
- Cross-protocol governance coordination
Content and Media
- NFT collection curation and management
- Automated content monetization strategies
- Intellectual property licensing and royalty management
Infrastructure Services
- Decentralized storage orchestration
- Compute resource allocation and optimization
- Network infrastructure management and monitoring
The key insight is that agents can process and act upon information at scales impossible for human participants, potentially unlocking entirely new categories of protocol utilization.
Implementation Diversity
Following the Ethereum client diversity model, we envision multiple compliant implementations:
- Reference Implementation: TypeScript/JavaScript for broad compatibility
- Performance Implementation: Rust or Go for high-throughput applications
- Embedded Implementation: Lightweight versions for resource-constrained environments
- Specialized Implementations: Domain-specific optimizations for particular use cases
All implementations must pass identical compliance tests and produce cryptographically equivalent results.
Ecosystem Implications
Security Properties
- Non-custodial: Agents never handle private keys directly
- Verifiable: All protocol interactions use canonical, audited implementations
- Transparent: Agent decision-making process fully auditable
- Composable: Clear interfaces enable sophisticated multi-protocol strategies
Network Effects
- Protocol Adoption: Agents can utilize protocols too complex for typical user interfaces
- Liquidity Provision: Continuous, algorithmic market participation
- Innovation Acceleration: Rapid iteration on protocol interaction patterns
- Accessibility: Complex strategies available through natural language interfaces
Path Forward
We propose the following development trajectory:
- Community Review: Gather feedback on architectural approach and security model
- Specification Development: Formalize interfaces and compliance requirements
- Reference Implementation: Build and audit canonical TypeScript implementation
- Registry Deployment: Deploy on-chain verification infrastructure
- Alternative Implementations: Support diverse implementation efforts
- Integration Support: Assist major agent frameworks with adoption
Request for Comments
This proposal represents a systematic approach to a complex challenge: enabling sophisticated autonomous agents to participate securely in Ethereum’s protocol ecosystem. We believe the separation of concerns architecture, combined with formal specification and compliance testing, provides a path toward safe agent-protocol interaction at scale.
Key questions for community consideration:
- Security Model: Does the proposed verification system adequately address trust concerns?
- Specification Scope: Are there critical protocol interaction patterns not covered by this approach?
- Implementation Strategy: What additional considerations are needed for safe deployment?
- Governance: How should canonical implementation maintenance and updates be managed?
The emergence of capable autonomous agents is not a question of if, but when. By establishing secure, standardized integration patterns now, we can ensure that when agents do participate in the network, they do so in ways that strengthen rather than compromise Ethereum’s foundational principles.