Staircase attack
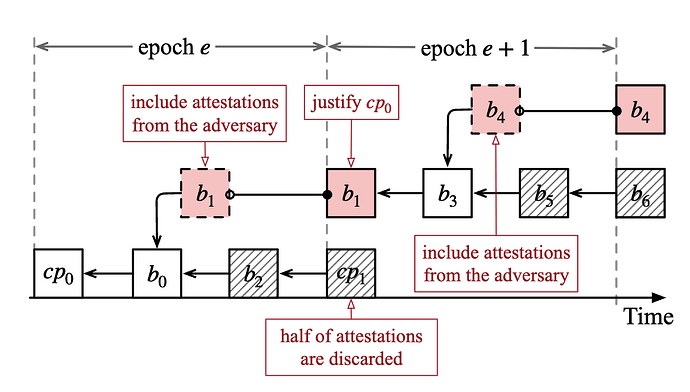
Staircase attack is a recent attack on the attestation incentives. Staircase attack aims to make honest validators suffer from penalties even if they strictly follow the protocol in a synchronous network after Capella upgrade. In staircase attacks, Byzantine validators withhold their attestations to prevent the canonical chain from justifying the last checkpoint. As illustrated in Figure 1, in epoch e, the Byzantine validators withhold their attestations to prevent the honest validators from justifying the checkpoint cp_0. The attestations from Byzantine validators are included in a withheld block b_1, a block proposed by a Byzantine validator. Before the middle of epoch e+1, all honest validators extend the chain led by block b_0. After the middle of epoch e+1, the withheld block b_1 is released. The last justified checkpoint is updated as only the withheld chain includes two-thirds of attestations for checkpoint block cp_0. The chain led by cp_1 is filtered in HLMD-GHOST and the chain led by b_1 becomes the canonical chain. In this attack, the attestations from honest validators in the first half of epoch e+1 are discarded, as the chain they vote for is not later finalized. These honest validators suffer from penalties according to the protocol. It was shown that by controlling 29.6% of the total stake, the attack can be conducted in every epoch so eventually all honest validators suffer from no incentive rewards. The attack was mitigated via the Deneb upgrade.
Staircase Attack-II
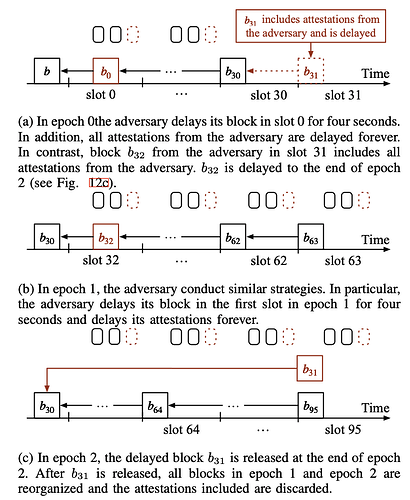
We find a new variant of the staircase attack and we called it staircase attack-II, as shown in Figure 2. Similar to the staircase attack, Staircase Attack-II requires the proposer in the first slot of an epoch to be Byzantine. Additionally, staircase attack-II assumes that the proposer in the first slot of epoch 1 is also Byzantine.
As shown in Figure 2, at the beginning of epoch 0, the adversary delays its block b_0 in slot 0 for four seconds. Therefore, the target of attestations from honest validators in slot 0, i.e., block b, is different from the target of attestations in slots 1-31, i.e., block b_0. In addition, all attestations from the adversary are delayed forever. Accordingly, the number of attestations from honest validators with the same target and source can not reach 2n/3. Block b_0, which is supposed to be justified in epoch 0, cannot be justified by the attestations from honest validators. In contrast, the adversary can justify the block in slot 0 by releasing its last block in epoch 0, i.e., block b_{31}. This block includes the attestations from the adversary, so the number of attestations exceeds two-thirds. The adversary delays the block for two epochs. As a result, the block in slot 0 can be justified at the end of epoch 2. In epoch 1, the adversary conducts the same strategies. Particularly, the adversary delays the block b_{32} for four seconds and delays all attestations from the adversary. Therefore, the honest validators can not justify the block in epoch 1. After block b_{31} is released in epoch 2, block b_0 is justified. As the chain from honest validators does not justify any new block, the chain led by b_{31} is the new canonical chain. All attestations included in the chain from honest validators are discarded.
Analysis
Our staircase attack-II shares the same feature as the staircase attack: Byzantine validators receive rewards but honest validators suffer from penalties, although honest validators strictly follow the specification of the protocol. Therefore, this attack falls into metric III in our criteria. The probability of launching the attack is 1/9, as we require the proposer in the first slot to be Byzantine. Unlike the staircase attack, staircase attack-II cannot be continuously launched. However, if the adversary controls 33% stake and launches the attack whenever the attack can be launched, \textit{all} honest validators will suffer from penalties for the corresponding epochs.