Elliptic curve addition is a pretty basic primitive, and those core primitives have been studied for years. So the optimizations are likely to come from aggregation, likely via caching aggregate (an engineering problem).
That said there are interesting research in large-scale BLS aggregation, see Web3 Foundation https://web.archive.org/web/20230124085821/https://research.web3.foundation/en/latest/polkadot/LightClientsBridges/index.html
And also RecProofs from Lagrange Labs as aggregation in SNARKS is very very expensive: https://www.lagrange.dev/recproofs
So zkBridges team and coprocessor teams that want to prove Casper in ZK (zkCasper) likely have some interesting optimizations to reduce the amount of work to do.
Now this is something I’m quite interested in and if people want benchmarks on various hardware, I can update the one I did for @asn for Devcon VI (Batch additions by mratsim · Pull Request #207 · mratsim/constantine · GitHub)
I’ll be happy to build any cryptographic optimizations into Constantine for actual measuremements.
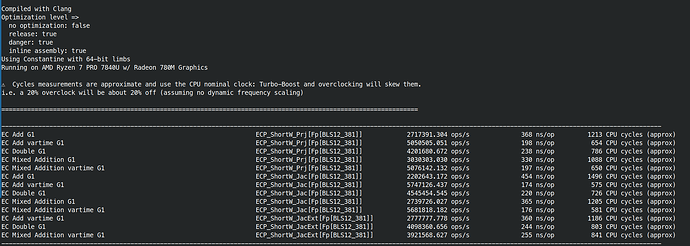
On my Ryzen 7840U (low-power, 15W, 8 cores, laptop CPU), individual EC add with various coordinate system:
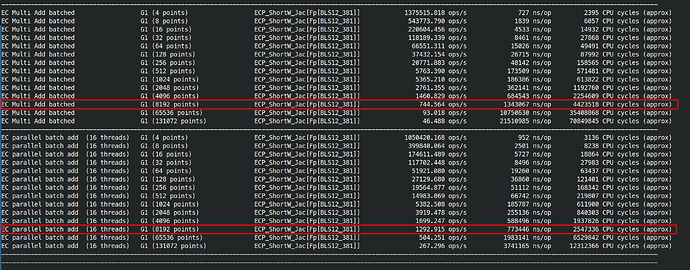
And with batch addition, serial and parallelized:
I think at 1.3ms, single-threaded, the cryptography is plenty fast, and the delay will be the aggregators’ topology and networking, see Signature Merging for Large-Scale Consensus