Unrealized manipulation attack
Building on the 3 kinds of one-epoch inactivation attack in [1] and collusive Byzantine strategies, we propose six new Unrealized manipulation attack strategies. These attacks exploit collusion among adversaries to keep the honest chain inactive, and then use a single adversarial block with sufficient votes to connect to an unrealized block and reorganize the honest blocks on the chain, causing losses to honest validators. The specific strategy below illustrates the idea:
Strategy 1
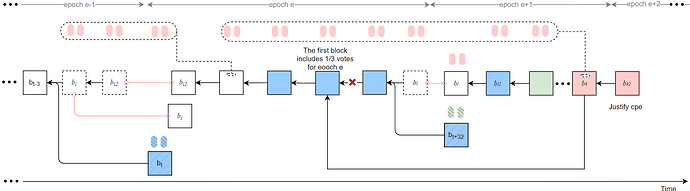
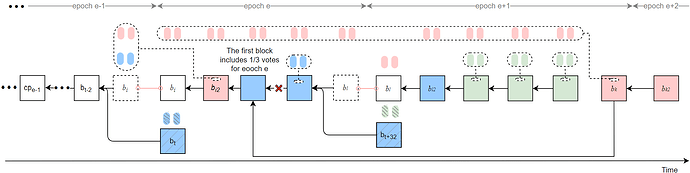
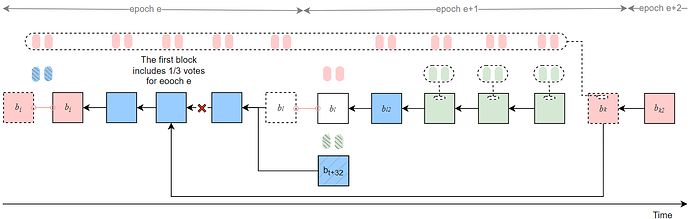
- During epochs e and e\!+\!1, except for slot t and slot t\!+\!32, all Byzantine votes are collusively sent only to the final Byzantine proposer v_k in epoch e\!+\!1. This proposer does not continue to extend the current honest chain; instead, it sets the parent to be the first block in epoch e that contains 1/3 voting weight (the block proposed at slot t\!+\!18), and withholds releasing b_k.
- Launch a sly-ex-ante attack against the honest validators in epoch e, and perform a single sly-sandwich attack against the honest validators in epoch e\!+\!1.
- In epoch e\!+\!2, the Byzantine proposer at slot t\!+\!64 proposes b_{k2} with parent b_k, and releases b_k and b_{k2} simultaneously within the first 4 seconds so as to justify cp_e and roll back the honest branch.
Strategy 2
- During epochs e and e+1, except for slot t, all Byzantine votes are collusively sent only to the final Byzantine proposer v_k in epoch e+1. This proposer does not continue to extend the current honest chain; instead, it sets the parent to be the first block in epoch e that contains 1/3 voting weight (the block proposed at slot t+18), and withholds releasing b_k.
- Launch a sly-ex-ante attack against the honest validators in epoch e, and perform one sly-1/3-slot-withhold attack against the honest validators in epoch e+1.
- In epoch e+2, the Byzantine proposer at slot t+64 proposes b_{k2} with parent b_k, and releases b_k and b_{k2} simultaneously within the first 4 seconds so as to justify cp_e and roll back the honest branch.
Strategy 3
- During epochs e and e+1, except for slot t+32, all Byzantine votes are collusively sent only to the final Byzantine proposer v_k in epoch e+1. This proposer does not continue to extend the current honest chain; instead, it sets the parent to be the first block in epoch e that contains 1/3 voting weight (the block proposed at slot t+18), and withholds releasing b_k.
- Launch a sly-sandwich attack against the honest validators in epoch e, and also launch a sly-sandwich attack against the honest validators in epoch e+1.
- In epoch e+2, the Byzantine proposer at slot t+64 proposes b_{k2} with parent b_k, and releases b_k and b_{k2} simultaneously within the first 4 seconds so as to justify cp_e and roll back the honest branch.
Strategy 4
- During epochs e and e+1, all Byzantine votes are collusively sent only to the final Byzantine proposer v_k in epoch e+1. This proposer does not continue to extend the current honest chain; instead, it sets the parent to be the first block in epoch e that contains 1/3 voting weight (the block proposed at slot t+18), and withholds releasing b_k.
- Launch a sly-sandwich attack against the honest validators in epoch e, and launch a sly-1/3-slot-withhold attack against the honest validators in epoch e+1.
- In epoch e+2, the Byzantine proposer at slot t+64 proposes b_{k2} with parent b_k, and releases b_k and b_{k2} simultaneously within the first 4 seconds so as to justify cp_e and roll back the honest branch.
Strategy 5
- During epochs e and e+1, except for slot t+32, all Byzantine votes are collusively sent only to the Byzantine proposer v_k in the last slot of epoch e+1. This proposer does not continue to extend the current honest chain; instead, it sets the parent to be the first block in epoch e that contains 1/3 voting weight (the block proposed at slot t+18), and withholds releasing b_k.
- Launch a sly-1/3-slot-withhold attack against the honest validators in epoch e, and launch a sly-sandwich attack against the honest validators in epoch e+1.
- In epoch e+2, the Byzantine proposer at slot t+64 proposes b_{k2} with parent b_k, and releases b_k and b_{k2} simultaneously within the first 4 seconds so as to justify cp_e and roll back the honest branch.
Strategy 6
- During epochs e and e+1, all Byzantine votes are collusively sent only to the Byzantine proposer v_k in the last slot of epoch e+1. This proposer does not continue to extend the current honest chain; instead, it sets the parent to be the first block in epoch e that contains 1/3 voting weight (the block proposed at slot t+18), and withholds releasing b_k.
- Launch a sly-1/3-slot-withhold attack against the honest validators in epoch e, and also launch a sly-1/3-slot-withhold attack against the honest validators in epoch e+1.
- In epoch e+2, the Byzantine proposer at slot t+64 proposes b_{k2} with parent b_k, and releases b_k and b_{k2} simultaneously within the first 4 seconds so as to justify cp_e and roll back the honest branch.
Attack Extension Strategies
In fact, the six attack strategies we described above are only the most basic “take-what-you-get” strategies. In real attack scenarios, we can further leverage the three kinds of one-epoch inactivation attack in [1] to keep additional epochs inactive, thereby amplifying the attack. For example, for the six strategies above, if the proposer at slot t+64 is Byzantine; or if the proposer at slot t+64 is honest while the proposers at slots t+63 and t+62 are both Byzantine; or if the proposer at slot t+64 is honest while the proposers at slots t+63 and t+65 are Byzantine, then the adversaries can proceed to launch a third-stage one-epoch inactivation attack that causes epoch e+2 to become inactive. Immediately afterwards, the Byzantine proposer in the last slot of epoch e+2 can set as parent the first block in epoch e that contains \frac{1}{3} of the voting weight, thereby rolling back an additional epoch of honest blocks and attestations…
By the way, for all the attack strategies above, if b_{k2} is the block of the first slot then it is unnecessary to launch a one-epoch inactivation attack against epoch e+1. If b_{k2} is a later block, then that one-epoch inactivation attack must be carried out.